Investigating the "Gartner, Forester, and Symantec say NVRs are the TOP Security Risk" Claim
We rate this statement as false.
What's the claim?
There's a security camera company that has been claiming that Gartner, Forester, and Symantec have called NVRs the TOP Security Risk in their most recent reports.
Security researchers almost never agree, so this should strike you as suspect from the start, but let's unpack this claim.
Who is Making the Claim
This claim is part of a section of their sales pitch which, depending on the salesman, implies or directly states that only their equipment is secure. This is absolutely not the case. Additionally, this company has made several claims that are part of this series and directly markets towards enterprise, corporate, and government-focused clients.
Gartner, Symantec, and Forester's Security Research
1. Gartner
Here's the link to Gartner's 2019 Top 7 security risk assessment.
As you can see, NVRs did not even make the list of the top 10 threats in Gartner's, let alone rank as the single greatest threat, as the claim suggests.
2. Symantec
Here's the link to Symantec's latest security assessment. You will have to trade your contact info (email, job title, name, and phone) for the ability to download it, so we'll document what the report says clearly on this page:
After a massive increase in Internet of Things (IoT) attacks in 2017, attack numbers stabilized in 2018, when the number of attacks averaged 5,200 per month against Symantec’s IoT honeypot. Routers and connected cameras were by far the main source of IoT attacks, accounting for over 90 percent of all attacks on the honeypot. The proportion of infected cameras used in attacks increased considerably during 2018. Connected cameras accounted for 15 percent of attacks, up from 3.5 percent in 2017.

An Assessment About Cameras Portrayed as a Recommendation About NVRs
The issues here are legion. First, Symantec is cataloging a threat, not making a recommendation, at all. Secondly, this is on page 20 and 53 respectfully. Not their #1 security threat by any stretch of the imagination. It is probably logical to assume that the first thing they mention in the report is the most important one, but Symantec doesn't even seem to explicitly rank security threats in this report. Thirdly, on page 20, they state "Routers and connected cameras were the most infected devices and accounted for 75 and 15 percent of the attacks respectively." Most importantly, Symantec's threat assessment was actually 100% opposite of the claims made by this company. The very thing that this company claims will lower your risk is that which Symantec says is the real risk.
This company recommends forgoing the NVR as a way to more properly secure your network, by claiming that Symantec recommends this. Symantec correctly has identified that the hacks have occurred mostly from cameras and routers.
Demanding that one should never use an NVR and instead put cameras directly on your network, because cameras got hacked, is crazy talk.
A Real Threat, Obscured
At another point in the report, Symantec said:
The notorious Mirai distributed denial of service (DDoS) worm remained an active threat and, with 16 percent of the attacks, was the third most common IoT threat in 2018. Mirai is constantly evolving and variants use up to 16 different exploits, persistently adding new exploits to increase the success rate for infection, as devices often remain unpatched.
We cataloged how IP cameras, including One Million Dahua (Lorex) cameras, have been affected with the Mirai botnet virus, in the "Consumer Grade Cameras are Often Used to Attack Critical USA Infrastructure" section of our "Best Practices for preventing IOT Security Camera Hacks" support advisory.
This security threat is incredibly serious and not easily fixed.
Why Does This Threat Exist? Why Doesn't Someone Fix It?
This threat exists because the processors put into IP cameras aren't used in much else. IP cameras and smartphones are remarkably similar in design but are worlds different. IP cameras are more reasonably priced than smartphones because they use budget processors that use hardware encoding, rather than software encoding to do their work. Smartphones use mostly software-based processing to create their videos. This is less efficient with video than a processor that can do one thing, but it allows your smartphone to do just about anything. Additionally, IP cameras use custom-designed embedded boards that connect to these hardware encoding processors, image sensors, and DSP chips. Lastly, smartphones are easier to maintain because there's either a limited number of hardware configurations (Apple) or a common underlying OS (Android).
By taking what is pretty similar to a phone, swapping out the multi-function processor for one that specializes in video encoding, and then removing everything unnecessary, IP camera prices are 10% of smartphone costs, but these modifications have another cost--time.
Most camera systems use a version of either QT and C++ code or Node.js as their firmware. The problem is that the latest versions of Node.js, for example, only support the latest and greatest processors and standard board configurations--the kinds in flagship PCs or $900-1500 phones and phone hardware designs. That means that automatic security updates from Node.js aren't included by default and can't run on the custom camera hardware without changes anyway. This means that once Node.js recognizes a hack, gets a fix published, the camera hardware manufacturer has to take that fix and make it work in their custom hardware environment. Then the customer has to install the fix on their device. This is not a nimble environment that can respond to security threats easily.
The cameras that the false-claimant company buys are rebranded versions of Vivotek hardware with an additional software layer both in the cloud and on the device. There are some good ideas with those implementations, but also some cybersecurity risks. Let's break them down:
1. Custom firmware is a great idea. It probably does make the cameras more secure, but only through obscurity. The delay in making the Node.js security update compatible with their custom hardware will always be baked in. As soon as their product becomes sufficiently popular, hackers will look to exploit it, too. This will greatly depend on how much customization has actually happened to the Vivotek cameras. For example, are any of Vivotek's known exploits still present? First example. Second example. Third example.
2. Cloud based two-factor authentication is a great idea. It allows you to keep the camera from "hacked" by someone guessing your password. This is not the real threat, however. It has nothing to do with the Mirari botnet or the speed in fixing known exploits on custom hardware designs.
3. A small yearly or monthly fee is a great idea. The reason for this is that right now, the creators of IP cameras have no financial or legal requirement to make sure that their equipment is secure after they sell it to you. Maintaining a secure codebase that adapts to current security threats is expensive and right now is not priced into any financial models, nor required by any contracts. The industry is being exploited by hackers in a way it never had before, and cybersecurity contracts must change to become part of the product cost, much in the way that the traditional maintenance service rider is usually part of any integrator's bid or the way that "guaranteed security updates" are included as part of phone contracts.
The Only Reasonable Solution
You just can't make an IP camera truly secure, because the time it takes a known exploit to be fixed has too many steps on custom hardware and each model has its own custom hardware.
The only reasonable solution is to hide the cameras from the network.
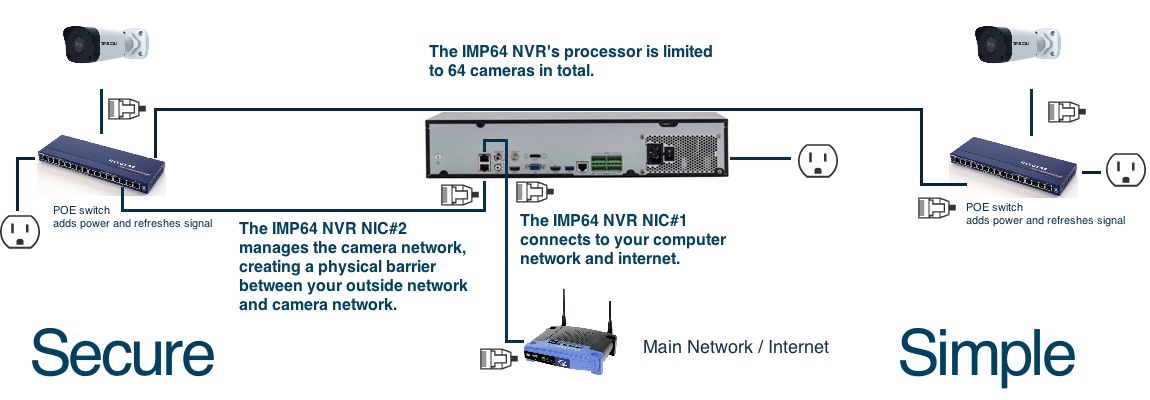
Here at SCW, that's what we do. The cameras plugged into the Admiral line NVR's POE ports directly or plugged into the Imperial Line NVRs Lan2 Network directly are not visible or accessible on your computer network. They run on an isolated network similar to an air gap. The only way to access these cameras is to plug a computer into those POE ports or hack into the NVR. There's a physical barrier from the cameras to the main network. In addition, there's also a subnetwork running on the NVRs, which means that even if you do plug a computer into the NVR's physically separate, isolated network, you would also need to know their subnet mask.
For example, here's how our NVRs work:
Do this.
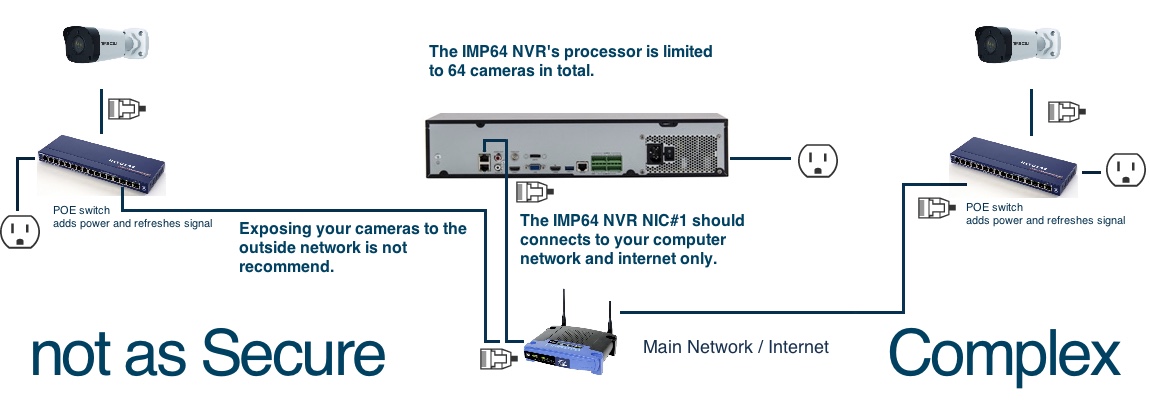
Try not to do this.
NVRs are Hacked Far Less Frequently
NVRs usually use more PC-like hardware and embedded Linux firmware. They don't have anywhere near as many models to maintain and the hardware configurations don't have a ton of variety, so they do tend to get more timely security updates.
This is not to say that NVRs are perfect and have never been hacked. NUUO, for example, was affected by the Peekaboo bug which gave unauthorized access to viewing camera feeds. NUUO NVRs were also used in the Reaper BotNet. In addition to the 1,000 Dahua cameras that were part of the Mirari botnet, some of their DVRs were also compromised.
Like any other product, there are companies with good track records of cyber security and bad records of cybersecurity.
3. Forester
Here's the link to Forester's latest security assessment.
Again, Forester's research did not seem to mention NVRs at all, let alone state that they were a top security threat (which was geopolitical in nature).
Forester's second top choice was: "Cloud Expansion And Vendor Consolidation Represent Top-Of-Mind Security Concerns" which they specifically mention "complaints of fragmented and siloed technology" as being a major issue.
We think that you should look at this research more closely. It does not vindicate this company but actually condemns them. Rather than using the open ONVIF standard, this company requires you to use their "fragmented and siloed technology" cloud-based viewer to watch their cameras.
Their cameras are not compatible with any third party software.
Just as Forester says one way of making a more secure product is creating a "fragmented and siloed technology." This is just a way that Forester recognized in solving one security problem by making another one. This is a threat of its own.
The whole reason that security updates take so long with the security camera industry is because of the custom hardware requirements and massive fragmentation in the industry. Creating more fragmentation isn't the answer.

Additional Claims made by the Same Source
EXPOSED - No, NVRs are not "A Single Point of Failure"
EXPOSED - No, NVRs are not "Outdated"
EXPOSED - No, HIPAA Compliance Doesn't Require 90 Days of Video Surveillance Footage
EXPOSED - No, You Probably Don't Need 90 Days of Video Surveillance Footage for PCI Compliance
Lean on the experts
We'd be happy to work up a custom quote or take your floorplan and create a security coverage map.
Get aCustom Quote







