Best Practices for preventing IoT Security Camera Hacks
The FBI has released a bulletin that recommends that you keep your IoT devices, like security cameras, on a separate network from your computers, which is exactly what SCW NVRs do.
Unsecured Security Cameras are Often Used to Attack Critical USA Infrastructure
Early in 2016, PC Word found a 25,000 camera network that was compromised and being prepared for an attack.
On Sept. 30, 2016, the Wall Street Journal found that several additional major manufacturers of security camera were hacked in a different attack, and the cameras and recorders were used to wreck havoc on US companies and network infrastructure, resulting in massive amounts of lost productivity when the internet was down for nearly twenty-four hours in most of the USA.
Vice news called this Mirai botnet, in 2016, "the biggest attack we've ever seen."
***
On Sept 25th, 2017, Dahua (Lorex), a major competitor of SCW, had all of their camera systems hacked and put into the Mirai botnet and customers lost their video feeds.
On Oct 23rd, 2017, Forbes called the vulnerability "The Next Web Crisis" since the hackers have access but have hardly used the devices, yet.
On Nov 15th, 2017, The Washington Post claimed that Dahua (Lorex) added this backdoor "deliberately based on the way the code was written."
It is estimated that over 1 Million Dahua / Lorex cameras have been affected by the Bashlight malware.
Why Does it Matter?
You're probably thinking, "I don't have anything important enough on camera for a hacker to look at, so this doesn't concern me," but that's not what's happening. The real issue isn't hackers looking into the camera feeds (although that can be a very big invasion of privacy) as much as they are using the camera's processors to do something that the camera was not designed to do.
A Processor is a Processor, Whether it is in a Camera or a Computer
Just because a camera is programmed to take video doesn't mean that its processor can't be reprogrammed to watch for credit card numbers being transmitted across your networks, or catalog and copy all internal documents or emails, or be used to send outgoing messages or requests.
Some installers of cheaper systems are reporting things like, "One of our property managers had her bank account compromised because of the back door access to her network, through this camera" or the Dec 9 2021 hack reported by Forinet which claimed "we observed numerous payloads attempting to leverage this vulnerability to probing the status of devices or extracting sensitive data from victims [computer network]. One payload in particular caught our attention. It tries to drop a downloader that exhibits infection behavior."
Other's are reporting wide-scale disabling of camera feeds. Most troubling is that some hackers are using the cameras to create a botnet.

What's a Botnet?
A botnet is a collection of internet-connected devices (things with processors) that have malicious code on them that can be used to collectively attack other high-value targets. Botnets can include PCs with viruses or IoT (internet of things) devices like smart thermostats or security cameras that have malware or have such easy access to their administration accounts, that they can be collectively controlled by remote code execution. In other words, a botnet is when 10,000 or 10,000,000 devices with a processor (like most modern security cameras) can be controlled in mass remotely, and are directed to perform a DDOS attack (Distributed Denial of Service).
What is a DDOS (Distributed Denial of Service) Attack
DDOS is basically the computer equivalent of someone who interrupts you repeatedly, but millions of times a second. A DDOS attack is a type of cyber warfare that brings down servers by giving those servers an unprecedented number of requests at such a frequency and scale that the server just gets overwhelmed and can't process anything. This causes it to crash and have to reboot.
This may sound like it is not a big deal, but it is.
Because servers are more vulnerable when rebooting, this can expose them to have malicious code injected into them during this reboot process. Also, there are types of servers that really should never be rebooted--the energy grid or your ISP hubs, for example. If you bring the dozens of servers that maintain an energy grid, down simultaneously, you can blackout or part (or all) of a country. Blacking out critical military tech, like battlefield communications, or GPS location data can result in loss of life and change the outcome of a battle.
The reality is that the processors in low-cost security cameras are being used to attack critical US infrastructure by hostile foreign actors. Nuclear power plants, military tech, and Internet Service Providers are at risk. This is also why Congress recently banned several security camera equipment manufacturers from federal jobs.
People are Human, and Forget Passwords
All devices that use a password need to have a "forgot password" override protocol. The reality is that we're all human and people forget passwords. You have to have a way to recover or reset it.
A good password reset procedure includes some safety protocols to make sure that you are who you claim to be. For example, when you forget your password for this website, you get an email to your email address. When you lose your password with an SCW camera, you have to tell us your name and order number (which usually involves logging into our website) so that we can reset the password for you.
A special username/password combo that works on all devices, that a manufacturer can use to look at your camera feed, is not a good password reset procedure. That's a backdoor.
What's a Backdoor?
A backdoor is a "super admin" user for a device that has the ability to remove the customer's user account. It differs from a good password procedure in that it isn't locked behind some sort of secure customer-supplied unique information. It just works on everything.
In the last few years, several camera manufacturers were found to have backdoor accounts in plain text and special manufacturer credentials.
The biggest problem with a backdoor account is that they often get leaked.
What SCW does to Prevent IoT Hacks
SCW Secure: an Isolated Network within a Network
The first goal in any cyber security plan is to reduce your threat footprint. If you have fewer devices on a network, there are fewer things that can be hacked. Properly connected, SCW NVRs will do this for you.
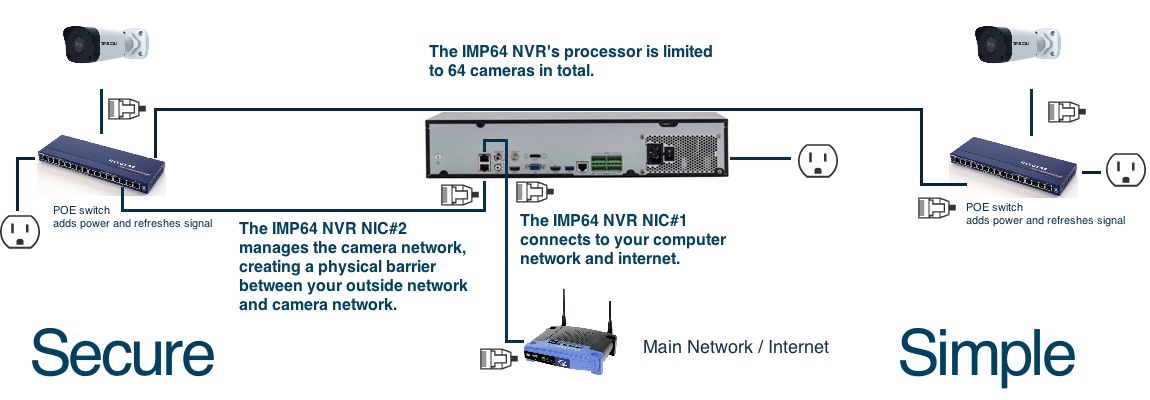
The cameras plugged into the Admiral line NVR's POE ports directly or plugged into the Imperial Line NVRs Lan2 Network directly are not visible or accessible on your computer network. They run on an isolated network similar to an air gap. The only way to access these cameras is to plug a computer into those POE ports or hack into the NVR. There's a physical barrier from the cameras to the main network. In addition, there's also a subnetwork running on the NVRs, which means that even if you do plug a computer into the NVR's physically separate, isolated network, you would also need to know their subnet mask.
Good for More than One Reason
This has several additional advantages:
1. Faster Networks. Unlike traditional NVRs, when plugged into our NVR’s isolated network, the camera's video feeds do not slow down your main computer network.
2. Isolated Cameras. Since they are on both a physically separated network and a subnet, your cameras are not visible on your computer network or to outsiders. You can connect to the NVR remotely and log in and then use the NVR as a bridge to watch the cameras, but neither you nor a hacker can log into the cameras without either logging into the NVR or being physically present to plug into the NVR and possessing knowledge about your NVR's specific camera subnet mask. (You can customize this camera's subnet if you want). Of all security camera IoT hacks, 99% are through the cameras, not the NVR.
3. Less maintenance. Our camera line has one-click firmware updates straight from the NVR/Camera, meaning you don't even have to search for, find, or download the footage on a computer. You just click a button when using the device and update the firmware automatically. Therefore, the update process is not difficult. In addition, you don't have to worry about updating the cameras for cybersecurity reasons, since the NVR is the only device that can be accessed remotely. It is much easier to keep one device up to date than dozens or hundreds.
Best Practices for Preventing IoT Security Camera Hacks
1. Change your password.
Change your password. Change your password. Change your password.
Seriously, change your password. The number one rule in preventing security camera hacks is to change the default password!
We publish the default password for our devices on our website. If you don't change the password, assume anyone who can do a five-minute Google search has access.
2. Plug the cameras into the POE ports on the back of our Imperial/Admiral NVRs.
All of our NVRs have the ability to record cameras on your main, computer network. This is insecure. Avoid this whenever possible.
All of our NVRs have the ability to record cameras from a remote location through the internet. This is extremely insecure, please do not do this. Most externally facing networks also do not have the ability to handle the amount of data that a 24/7 HD security camera creates. You'll get bad video and framerate results from this and you’re very likely to be hacked. Please do not do this.
Do this.

Try not to do this.
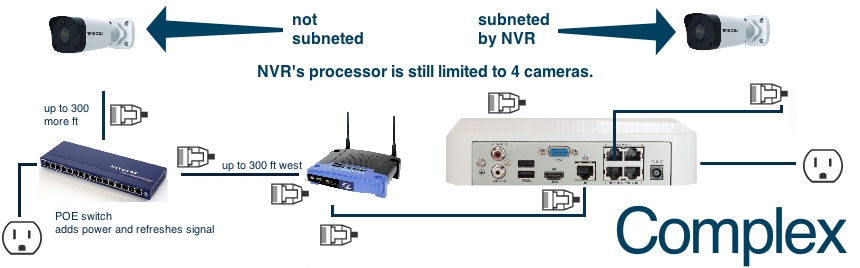
By plugging the cameras into the POE ports on the NVR, you use the physically separated network and subnet built into the NVR. This will separate the cameras off your main network by creating a sub-network (subnet) for the cameras. The number one rule regarding hacking is that you can't hack what you can't connect to. Plugging the cameras into the POE ports on the NVR will create a physical barrier between your cameras and your network, the NVR.
3. Use the NIC#1 on our Admiral/Imperial lines to connect to your computer network and NIC#2 to make a physically separated network and subnet for your cameras.
Do this.
Try not to do this.
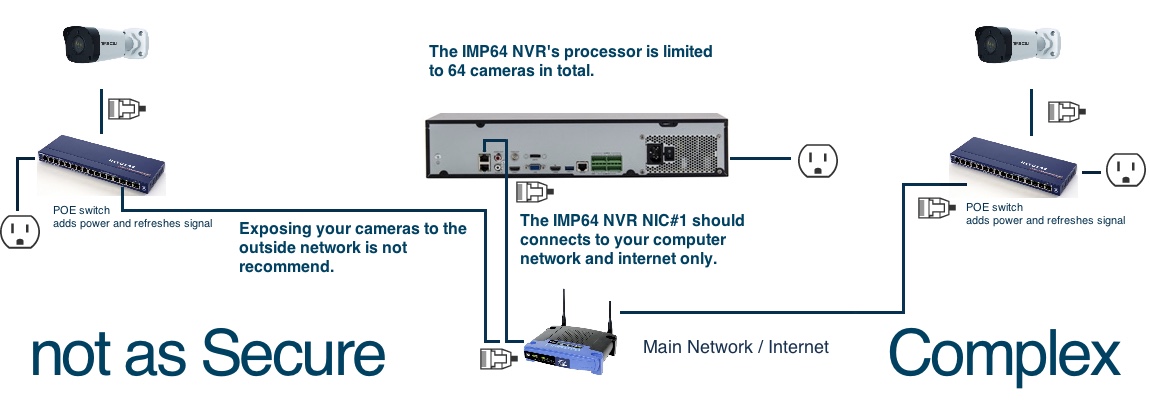
Although it is possible to add our cameras to your main network, it is always advisable to separate your camera network physically from your computer network. Even in situations where you have no internet connection, this is preferable as it keeps your main computer network from getting congested by all that video footage being transferred by your surveillance system. Again, you can't hack what you can't connect to.
4. In the event that you can't physically separate the network, corporations and large businesses should have their network administrators VLAN the cameras.
A VLAN is a Virtual Lan, which creates a hidden network within your network that only other devices on that VLAN can see. It is the virtual (which is the V) equivalent of the physical barrier created by subnetting your cameras.
In short, you can't hack what you can't see.
Disclaimer: No company can ever make a hack-proof product that you can view remotely. However, if you use our products in the way that we recommend, your cameras should not be visible on the network at all. Only the NVR should be on the network and the security in an NVR is usually a great deal better than in the cameras. If you are hacked, having to upgrade one NVR's firmware is a whole lot easier than that of dozens of cameras.
5. You probably want to VLAN the NVR, too, if you work for the government or a major corporation.
We can help you set this up if you have a VLAN already. Sorry, but we can't create a VLAN for you.
